AD
AD Labs
Capsulecorp
Game Of Active Directory
SCCM / MECM
Exchange
Winning GOAD
Bank Security Challenge
The Path to DA
Tools
BloodHound
Setup
Quick start:
Boost neo4j performance via memory configuration tweaks (recommended value is 1/4 of total RAM):
Quick start:
Import custom queries from legacy BloodHound (can be also done manually):
BloodHound.py BHCE branch:
Reset ALL:
To convert legacy BloodHound dumps to BHCE one can use bloodhound-convert.
Collectors
SharpHound.exe
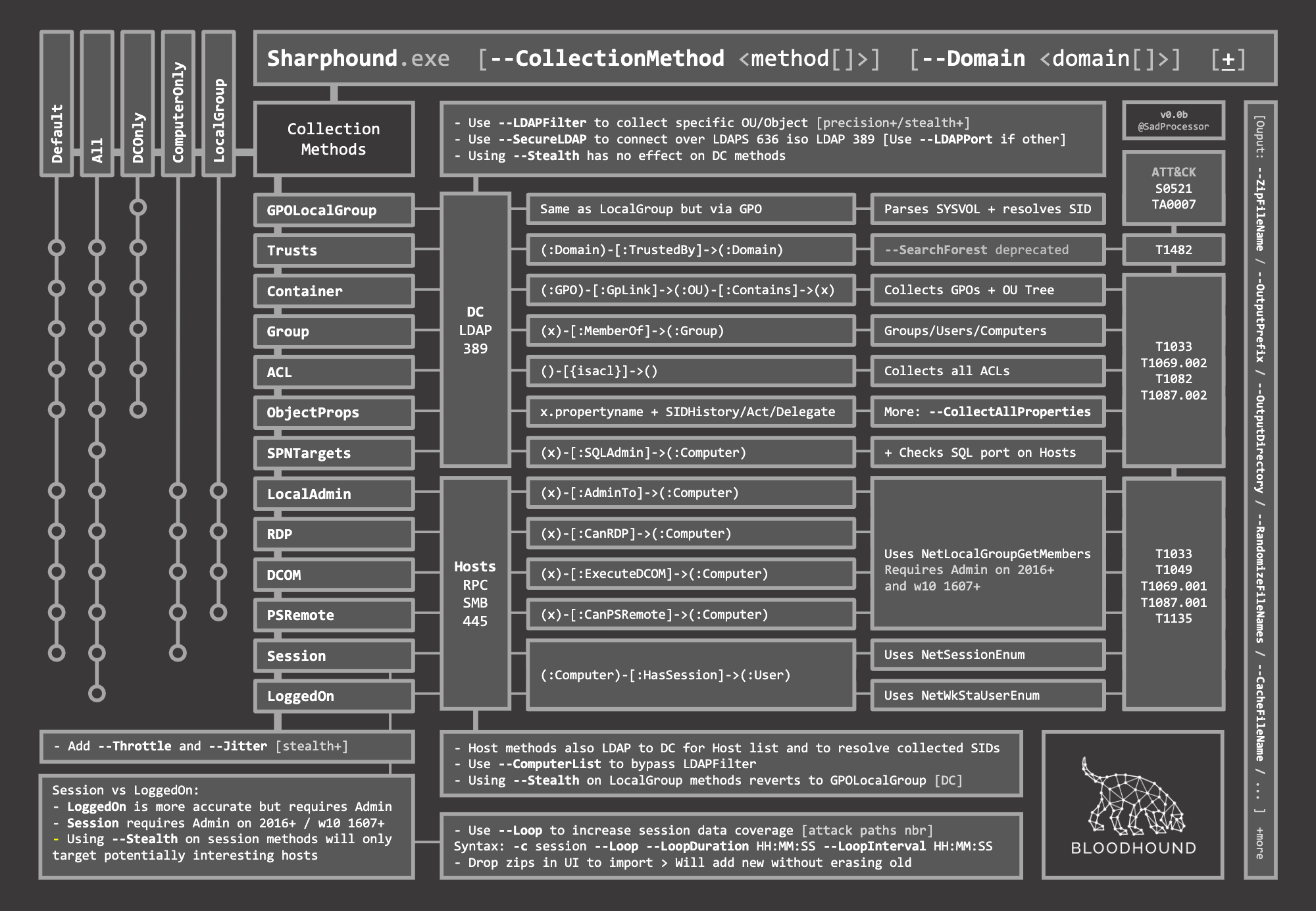
SharpHound.ps1
BloodHound.py
Import with bloodhound-import:
RustHound
ADWS
BOFHound
Install:
An example of manual AD CS data collecting:
Resolve a SID:
Resolve group memebership:
Parse:
ADExplorerSnapshot.py
You may also want to patch the (objectGUID=*) IoC in ADExplorer64.exe with a HEX editor ;)
Cypher (Neo4j)
Show percentage of collected user sessions:
Show path to any computer from kerberoastable users:
Manual JSON Parsing
There're 2 global dicts in JSON files: data and meta. We care about data:
List all active user accounts:
List non-empty user accounts' descriptions:
List user accounts whose passwords were set after their last logon (an effective list for password spraying assuming that the passwords were set by IT Desk and may be guessable):
List user accounts with DoesNotRequirePreAuth set (aka asreproastable):
List user accounts with SPN(s) set (aka kerberoastable)
List computer accounts' operating system names:
Make a list of all SQL servers (can be extrapolated to any SPN-based service):
Recursively list all members of a group (mimics RSAT Get-ADGroupMember, script):
Recursively list all groups which the user is a member of (mimics RSAT Get-ADUser | select memberof, script):
Generate a .csv file containing AD trusts mapping to be used in TrustVisualizer (mimics PowerView Get-DomainTrustMapping, script):
PowerView / SharpView / powerview.py
Example Queries
Users
Convert SID to name and vice versa:
Extract all domain user accounts into a .csv file:
List domain user accounts that do not require Kerberos pre-authentication (see ASREPRoasting):
List domain user accounts with Service Principal Names (SPNs) set (see Kerberoasting):
List domain user accounts with Kerberos unconstrained delegation enabled:
List domain user accounts with Kerberos constrained delegation enabled:
Search for domain user accounts which may have sensitive stored in the description field:
Search for domain user by email:
Find users with DCSync right:
Groups
Enumerate domain computers where specific users (Identity) are members of a specific local group (LocalGroup):
Computers
Extract all domain computer accounts into a .csv file:
List domain computer accounts that allow Kerberos unconstrained delegation:
Resolve all domain computer IPs by their names:
List domain computers that are part of a OU:
Shares
List shares for WS01 computer:
GPOs
List all domain users with a 4-digit RID (eliminates default objects like 516, 519, etc.) who can edit GPOs:
Resolve GPO ObjectDN:
Impacket
Install:
Static Binaries
Build Examples
{Crack,Sharp,Ps}MapExec / NetExec
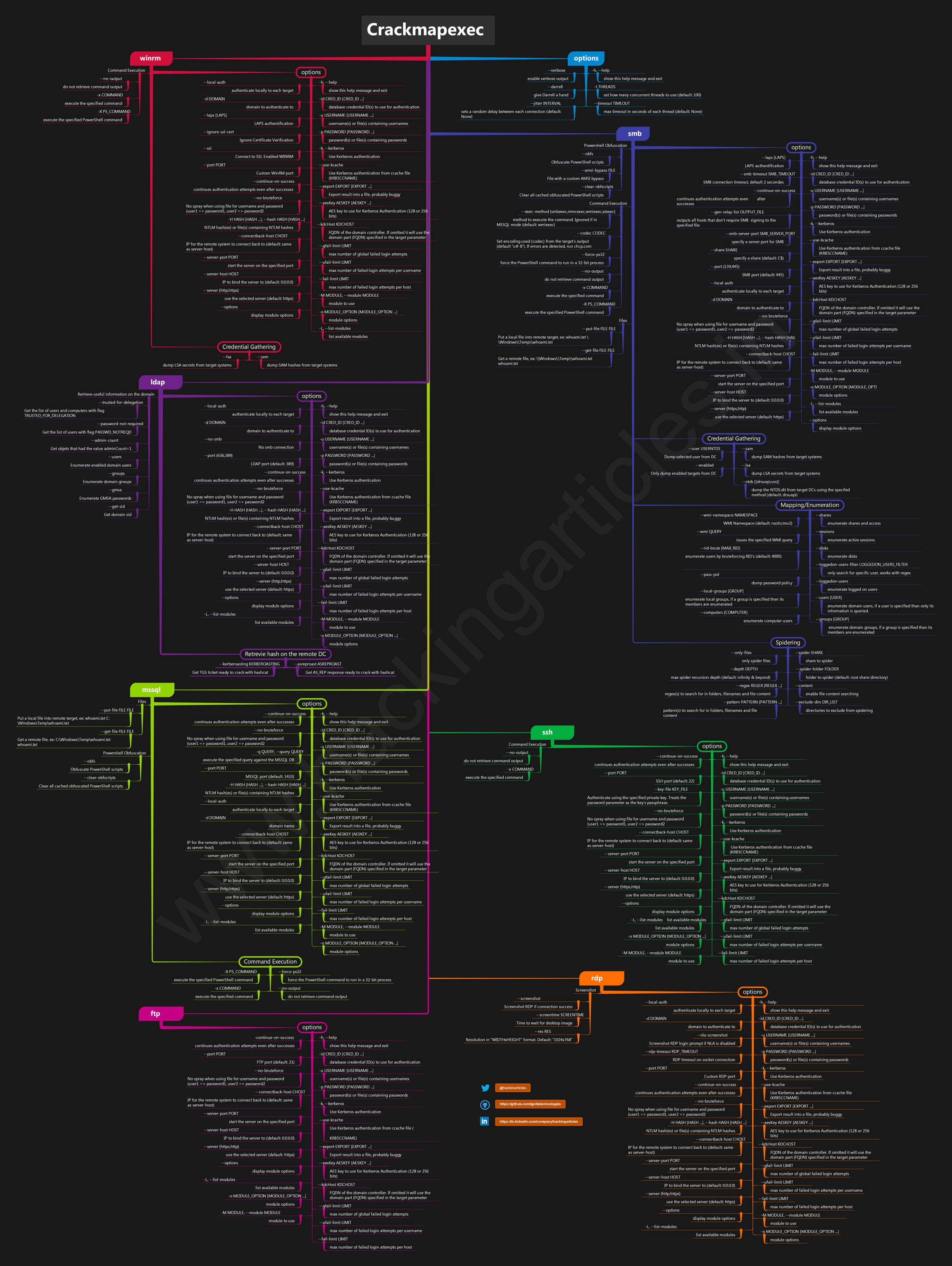
Install bleeding-edge:
aardwolf requires Rust compiler to be also installed:
Install for debugging and development:
Execute a PowerShell command using base64 encoding on-the-fly:
Bypass network IPS restrictions:
Custom Switches
Bypass execution restrictions of EDRs monitoring for WmiPrvSE.exe misbehavior with custom switches (see dotnetassembly branch).
Get the dependencies and stuff:
Example of invoking a PowerShell module (ConPtyShell):
Example of executing a .NET assembly (Rubeus):
Example of converting an unmanaged binary (NanoDump) to a shellcode with donut, then compiling a .NET self-injector from a template with the shellcode inside and executing it (see SharpBin2SelfInject):
aiosmb
Install:
Usage:
Slinky Cat & OffensiveSysAdmin
Mitigations
Common vulnerabilities & misconfigurations and recommendations:
SMB lateral-movement hardening:
Antispam protection for Exchange:
Detect stale, unused or fake computer accounts based on password age (replace -90 with your domain's maximum computer account password age):
Administrative Tier Model & Microsoft RaMP (Zero Trust Rapid Modernization Plan):
Post compromise AD actions (checklist):
Hardening automatization tool:
Last updated